The Australian OSINT Symposium 2025 brings together open-source intelligence (OSINT) practitioners, leaders, analysts, and researchers to advance tradecraft, harness AI, and strengthen intelligence capability.
The theme, Building Enduring OSINT Capability, addresses how to sustain OSINT at the individual, team, and organizational levels in an era of rapid technological change and global complexity.
Australian OSINT Symposium 2025
Date: September 18-19, 2025
Day 1 Takeaways
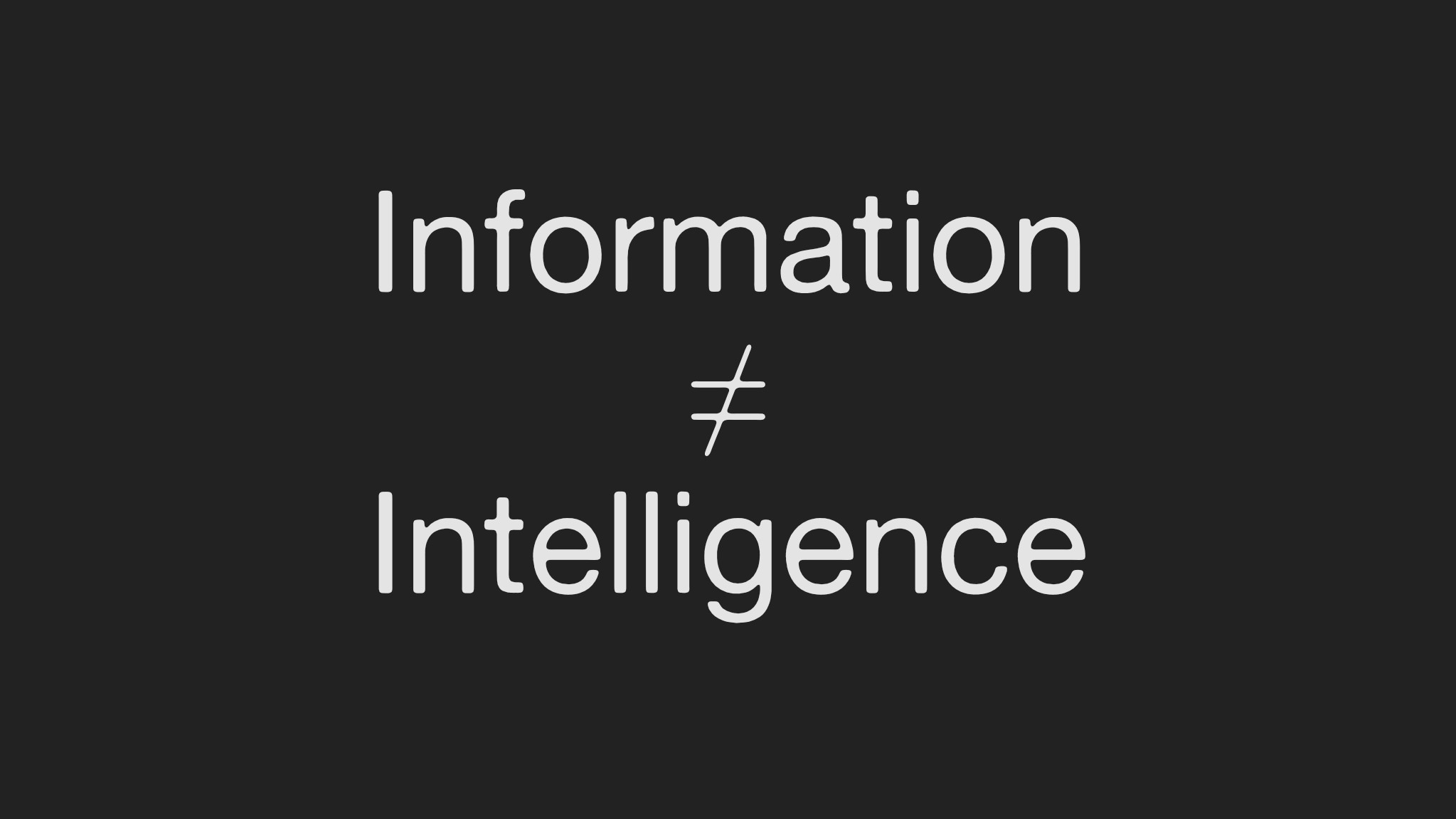
Information ≠ Intelligence
On Ethics and Trust
Sessions underscored that raw data has no value without context, verification, and accountability. One speaker compared journalism and OSINT, arguing that publishing information without ethical judgment risks harm to vulnerable communities. Examples ranged from footage of war crimes in Sudan to the choice not to film prisoners in Afghanistan. The erosion of public trust in journalism was a warning: without professional standards, OSINT could face the same fate.
On Generative AI in OSINT
Another session detailed how generative AI is reshaping investigative work. Analysts are experimenting with multimodal models, custom GPTs, and autonomous “agent mode” tools to speed up deep web research, map infrastructure, and investigate disinformation. AI can deliver 80% of results quickly, but human oversight is needed for accuracy and verification. Risks highlighted included sabotage, bias, hallucinations, and synthetic content threats such as deepfakes and extortion attempts.
On Espionage Tradecraft
Findings from over 930+ documented cases of Chinese espionage were presented. Unlike Western “non-traditional collectors,” China normalizes participation from students, academics, businesses, and local officials. Targeted technologies include semiconductors, aerospace, biotech, and energy. Motivations were reframed under a “BEWARE” model: Business opportunities, Ethno-nationalism, Wealth, Academic advancement, Repression, and Emotional bonds.
On Practical Investigative Techniques
This talk demonstrated hands-on OSINT methods. These included archiving profiles with the Wayback Machine, checking Facebook edit histories, reverse image and video searches, exploiting document metadata, and manipulating URLs for higher resolution content. Sock Puppet account management and operational security were emphasized, along with rigorous documentation and evidence handling using tools such as forensic extensions for Chrome. The message was clear: tools amplify errors without proper methodology.
On Executive Protection
Discussions on “digital executive protection” showed how OSINT supports situational awareness for executives and their families. Key steps included mapping digital footprints, training families about oversharing, and distinguishing between direct threats and operational disruptions. Case studies of activist monitoring at international events illustrated how analysts can provide actionable intelligence in real time, sometimes more usefully as a text alert than as a polished report.
On Trust in User-Generated Evidence
Research examined how courts and jurors treat citizen-captured videos in atrocity cases. Deepfakes increase the danger of the “liar’s dividend,” where authentic evidence is dismissed as fake. Judges stressed corroboration, metadata, and expert input, but even respected investigators could not always overcome juror skepticism. Realism in footage increased trust, but edits and unknown sources undermined it.
On Human Costs and Resilience
One talk focused on psychosocial risks for analysts: exposure to violent content, extremist propaganda, or child abuse material imposes long-term costs. Building enduring capability means investing in “presilience” — proactive measures for analyst wellbeing, not just recovery after harm. Balancing activism, advocacy, and structured analysis was another theme, ensuring decision-makers do not confuse passion with objective intelligence.
——
Across day 1, speakers kept circling back to the same anchors: tradecraft, timing, and trust. Without them, OSINT risks the same collapse in legitimacy that has already reshaped journalism.
Day 2 Takeaways
On The Illegal Empire
A global illicit economy worth $4.2 trillion connects counterfeit goods, human trafficking, and terrorism financing. Profits from fake sneakers (through Belgium) funded the Charlie Hebdo attack. A case study traced containers of counterfeit cigarettes from Southeast Asia that returned filled with trafficked women and girls. OSINT, blockchain tracing, and community tips enabled raids, seizures, and rescues. This organization reported 1.7 million actionable tips in 2023, leading to $2.5 billion in narcotics seized and more than one million arrests.
On Applied OSINT Against Trafficking
The presenters described their evolution from eight volunteers in 2020 to a structured task force of more than 150 analysts. They validated cases during live operations, ensuring intelligence was both actionable and legally sourced. In one case, traffickers and victims were identified within minutes, leading to arrests hours later and immediate victim support. The team emphasized delivering the “40% solution” quickly rather than waiting for perfect intelligence, stressing that intel must drive operations.
On Scaling Security in a Global Tech Firm
Protective security at a fast-growing company had to be built from scratch for a workforce of 3000 across 29 countries. Early steps included ruthless triage of risks, borrowing monitoring tools from marketing and cyber teams, and prioritizing operational hires before analysts. Communication proved critical: leaders responded better to concise Slack messages, visuals, and actionable “so what” analysis than to lengthy reports. Diverse teams and networks were highlighted as essential to resilience.
On Operational Security in OSINT
Practical OPSEC lessons underscored how investigators underestimate their digital footprints. VPN choices, browser fingerprints, mobile IPs, and even fitness apps can expose identities. Overly rigid workflows, like always building “sock puppets” the same way, increase detection risk. The message was to balance blending in with personal safety and adapt OPSEC to mission context. Every contact leaves a trace, and mistakes should be treated as learning opportunities.
On Managing OSINT Toolkits
An ADAPT framework — Assess, Discover & Align, Analyze Vendors, Procure, Track — was presented as a cycle for sustainable toolkit management. Redundant tools, underutilized features, and procurement without pilots waste resources. A failure case described a high-profile tool bought for its name but abandoned due to latency and poor adoption. A success case showed how piloting and early integration planning saved costs and improved satisfaction. The approach cut one client’s expenses by 30% while enabling long-term growth.
On Critical Infrastructure
Representatives from ports, healthcare, nuclear regulation, and academia discussed how OSINT supports resilience. Insider threats were highlighted — every recorded theft of radioactive material involved insiders. Remote work complicates risk detection, making OSINT vital. Sharing intelligence through trusted networks was described as faster and more effective than formal channels. Future priorities include managing fourth-party supply chain risks, overwhelming data volumes, and ensuring OSINT is integrated into business risk management.